How Tariffs, AI, and Robots Will Reshape Industry and Humanity
Tariffs are breaking old trade ties. AI and robots are rewriting the rules. The U.S.–China split is just the beginning of a new world map drawn in algorithms, not alliances.
Why does the Indian Election result look like an 'a la carte' menu served on an unexpected platter? Are we looking at something more than meets the eye?


Was the Indian Elections result a "pick and choose" or a natural consequence?
It looks less of a result and more of a message!
A victory this customized for a certain narrative to be a random occurrence will need to work against heavy odds!
It is as if seats were picked from an a la carte menu. All to drive home a message while pushing for the defeat of a certain group.
Let us look at one such occurrence to drive home the point.
The narrative being thrown around for why people in Ayodhya did not vote for BJP is that their lands were taken with no recourse.
It is flimsy at best.
Why?
Because Faizabad has 11 lakh votes. How many families out of 11 lakhs do you think would have been affected, if at all, by the land acquisition? Lakhs?
This is cover fire for something else.
Are we all being nudged by narratives to force-fit blame for a loss that may have been because of a set of events that we may not even be aware of?
Reports say that Modi had seven emergency meetings for weather-related arrangements before the counting had to start, while his ministers were meeting with the Election Commission.
Was Modi salvaging what he could at that last moment?
To save 2024 from becoming another 2004?
Let us look at a hypothetical script. We are not asserting anything. Merely discussing possibilities out there and looking in a direction we wouldn't have looked at otherwise.
What we do takes a lot of work. So, if you like our content and value the work that we are doing, please do consider contributing to our expenses. Choose the USD equivalent amount in your own currency you are comfortable with.
A Politician, let us call him "A" has been planning on rising on the back of a criminal and inherently corrupt plan. To lay the stage for his career, he makes "fight against corruption by his rivals" his main attacking plank. Buoyed by that crusade, he gets elected and keeps indulging in corruption that he had planned all along.
As rumors about this corruption begin to circulate, Politician A preemptively accuses, let's call him Politician M of taking bribes and engaging in corrupt activities with various companies. So, Politician A calls for an investigation into Politician M's alleged misconduct, hoping to create a smoke screen that diverts attention away from his own actions. This way, Politician A aims to discredit Politician M and frame the narrative, making it appear that Politician M is the one guilty of corruption.
The Politician A could very well be Politician R as well. Could be anyone for that matter.
What does this get him and them?
The public and media focus on the allegations against Politician M, while Politician A's own corrupt activities remain under the radar, at least temporarily. Politician A's accusations create doubt and suspicion around Politician M, potentially damaging their reputation and political standing at least in the eyes of a few groups.
To push this further, Politician A (and his friends like Politician R) unleash obnoxious propaganda to abuse Politician M because now (basis the allegations, false as they may be) it is all morally justified.
Politician A's (and his friend R's) strategy works, because they successfully avoid scrutiny and maintain their power and influence, despite their own corrupt behavior.
This is known as Projective identification.
Does that sound familiar?
This is the most basic form of this strategy.
Let us take this up a notch.
Politician R, Politician A's buddy in the above example, has some very intelligent and smart and resourceful buddies.
Folks who are in the league of great minds that created something like this.
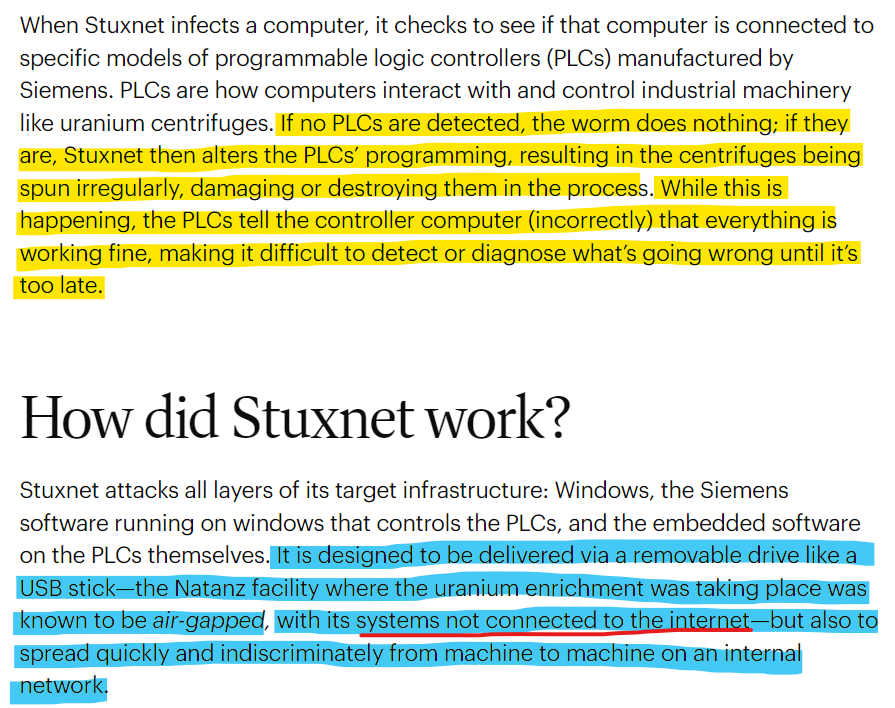
The facility was "air-gapped" (which means that every machine there was physically or digitally separated from anything that might try to reach it).
Yet, this virus built over 2-3 years by some of the most brilliant minds, was able to get in via a removable drive and able to proliferate around the facility to all systems, while checking what is going on and attack when the conditions matched the instructions.
Suddenly an entire nuclear reactor was destroyed.
Absolutely brilliant minds with enough funding are at the beck and call of the buddies that Politician A and R have.
They know every which way the followers and constituency of Politician M think.
Let us look into a hypothetical scenario.
Just as Politician M was planning his moves, so were Politicians A and R and their buddies.
A half-hearted campaign was launched - the Electronic Voting Machines are hackable and faulty so the country should go back to the paper ballot.
They knew the old reputation of the politicians of the decades gone by where elections were usurped by booth capturing and fake ballots. So paper ballots could not be an option for this group.
The followers of Politician M were raised on those machinations taking away every hope of power and dignity. Everyone in that ecosystem could never imagine a time where they could have access to power until the level playing field was created by a "non-hackable" Electronic Voting Machine.
So, how could the followers of Politician M even bear to imagine a world without the EVMs?
They went on with their full force of narrative and arguments against that suggestion. We cannot go back to the paper ballots and because you are questioning the EVMs we wont accept it.
Why?
Because, well they are god's gift to mankind and therefore so no one can even question their integrity.
In fact, some of Politician R's friends went as far as launching a farcical hackathon. All they wanted was to study one EVM for a year. (EVM hackathon)
It was a laughable event. But it did its work.
The stage was being laid for a long-haul strategy.
A repeat of an old story?

You see, power is a strange phenomenon. So is lack of it. An opponent promising to wipe you out is also giving you an impetus to go out and do everything that is in your wildest corrupt imagination to stop that person.
And, here the mantra was country free of such politicians.
The story against EVMs was launched. Laughed at, mocked and passionately argued by the Politician M's followers, the invincibility of the EVMs was sought to be established.
"EVMs are invincible" and no one was even willing to look at them to see if they really were that invincible?
Here is some story behind the cult of EVMs.
In February 2010, an international conference chaired by Subramanian Swamy criticized the Election Commission of India (ECI) for failing to ensure transparency in the functioning of Electronic Voting Machines (EVMs). (Source: Swamy for expert panel on secure EVMs / The Hindu)
Subsequently, in April 2010, a research team led by Hari K. Prasad, Rop Gonggrijp, and Alex Halderman released an independent security analysis. This analysis recommended transitioning to a more transparent voting system, such as paper ballots, precinct count optical scan, or a voter-verified paper audit trail (VVPAT). (Source: Security Analysis of India’s Electronic Voting Machines / The University of Michigan and Netindia (P) Ltd)
These systems would allow skeptical voters to observe the physical counting process, thereby enhancing confidence in the fairness of the election outcomes.
In 2011, a Public Interest Litigation (PIL) was filed in the Supreme Court, seeking a directive for the ECI to modify EVMs to print a slip with the symbol of the party for which the vote was cast.
On January 17, 2012, the Delhi High Court, in response to Subramanian Swamy's writ petition challenging the current form of EVMs, instructed the ECI to engage in broader consultations with the executive, political parties, and other stakeholders regarding the matter.

This led to further petitions in the Supreme Court, culminating in a 2013 ruling that mandated the implementation of VVPATs to enhance the transparency and reliability of the voting process. (Source: VVPATs for Vote Verification/ Supreme Court Observer)
What if the whole campaign against the EVMs was a decoy?
What if the response of the followers of Politician M was understood to be in a certain direction? And all this was an elaborate exercise in Projective identification?
What Politician M was being accused of, his opponents were planning just that?!
Let us look at the University of Michigan report we cited above. Please download it from the link - Security Analysis of India’s Electronic Voting Machines - and read it carefully.
We have brought the key points from it for your consideration.
Well, prior to that analysis, two attempts were made to check the reliability and security of the EVMs. All of them were facetious in their approach and actions.
How did these two committees draw their conclusions when they had no expertise in this area? Just see that both the evaluations were based on limited information and lacked rigorous independent testing. The committees did not have access to the source code and relied heavily on manufacturer presentations, which did not provide a comprehensive security assessment.
Here are some more strange measures that have their own issues.
Seals and Storage: EVMs are sealed with wax, string, and paper labels, and stored in various locations, including high schools and warehouses.
Pre-Election Testing: Small mock polls are conducted before each election to test the machines.
Masked ROM: The election software is stored in masked read-only memory, making it difficult to extract or verify.
Random Assignment: EVMs are randomly assigned to polling places to prevent targeted tampering. + Candidate Ordering: The final ballot positions are known only a few weeks before the election.
Third-Generation EVMs: Incorporate additional safeguards like a real-time clock and time-stamped logging.
What does this all tell us?
The report goes further to tell us how the whole election process can be rigged and gamed by someone to win elections.
Here are the 10 ways.
Did someone actually hack into the voting system in India? Unless a detailed investigation is done, no one will know. And if anyone did hack into the EVMs, the chances are that they would not have left any footprints.
But, why are we looking at this?
Because lately, allegations of election fraud from one side of the political spectrum have become far too common.
What is also common is that any discussion about possible rigging is met with the full force of a global system that does not even allow a discussion. In fact, any discussion is termed criminal.
Donald Trump and the aligned ecosystem have discussed at length about possible rigging in the 2020 elections. These are allegations as we said. Tucker Carlson articulated the issues on X.
Check this out.
🚨THREAD: Tucker Carlson on Duplicated Ballots, Falsified Tally Sheets, and Mail-In Ballot Fraud in Fulton County, Georgia
— KanekoaTheGreat (@KanekoaTheGreat) November 10, 2023
“It now appears there actually was meaningful voter fraud in Fulton County, Georgia, last November (2020). That is not a conspiracy theory. It’s true.… pic.twitter.com/qlyZIhQoX8
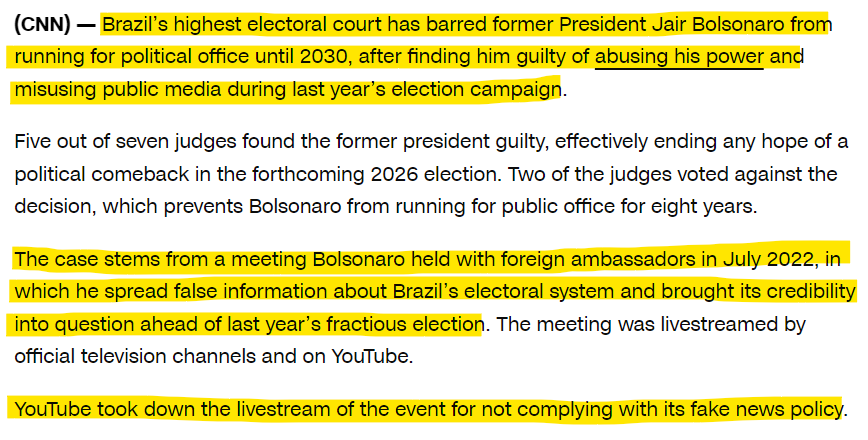
Similarly, the other major election in recent times was in Brazil. The then President Jair Bolsonaro made allegations of election fraud and even shared it with foreign diplomats.
Just that was enough to have him barred from fighting elections for 8 years.
Does that look normal? The pushback and the whole villainization of someone alleging fraud. Isn't critiquing the system a fundamental right?
Apparently not.
And it is a template.
What if this was to be the fate of another BRICS leader - Narendra Modi? Please read this on why BRICS is so important.

It is not that the leader was to lose but the leader was to be made persona non-grata in Indian politics so everyone in the vicinity could be targeted.
Everyone.
Hatred against him has been normalized in enough circles. Those people will not think twice when he is targeted along with others. As for the protests, they will be dealt with as if it was an act of terror.
If one has seen how Canada has handled the truckers protests or US has handled the Capitol January 6th attack, you can see where this could have gone.
But before that, one needs to go into history and check what was done by Nehru vis-a-vis the RSS.
It would be a repeat of that. Just at a more widespread level.
Riots instigated and people of a certain community targeted - backed by police.
We have seen that script unfold so many times in India.
How and why would it be any different henceforth?
After such a customized loss that targets the heart of everything that Modi has worked for, one needs to take some lessons.
Be a Krishna, Not a Chauhan: No matter how much Karna argued about the laws of war when his wheel was stuck, Krishna was clear. The edifice of rules that you have demolished yourself, you cannot seek refuge under that. Prithviraj Chauhan's lore needs to end. Where rules do not matter, they should not matter.
Corruption Clean-up cannot be a Top-Dressing: No matter how pure your intentions are, and how much you want to push integrity into the society, it will not take root until you uproot the whole system. That is impossible in a democracy. Changes like the one in Singapore, China, Malaysia and Korea happened simply because the regimes there were dictatorial. Democracy does not lend itself to such a massive change. So choose. Don't play cricket with a table tennis racket. It won't work!
Manage your Cadres: Even when Direct Transfers were done and the entire money went to the beneficiaries, the local politicians found enough leverage to get a cut. One person whom my family knows shared how it was the local BJP MLA who asked for Rs 7000 out of Rs 10,000 for a toilet. The rest was not enough for the toilet!
Create an Ecosystem: In 2021, comedian standup Munawar Faruqui was arrested for abusing Hindu Gods. He filed a bail application. The person who represented him in front of the Indore bench of the Madhya Pradesh High Court was Senior Advocate Vivek Tankha. (Source) First, advocates like him do not go easily to state high courts. Second, advocates like him charge Rs 5-10 lacs for one appearance. Where do you think Faruqui got the money to hire Tankha? Standup Comedy is an industry. YouTube video makers are an industry. Portals are an industry. Everyone is important and the other side invests heavily in them. You don't. Shame on you because folks backing you do it out of thankless love. It is not about your "values" but about a civilizational battle. You cannot fight an opponent who comes with an AK47 with a kitchen knife!
Revolutionaries of one Era are Moderates of Another: This was said by Bal Gangadhar Tilak. He did not allow Gandhi to start the Non-Cooperation movement while he was alive. Gandhi started a day after Tilak died. Time for moderation is over. The next big political wave to come out may well be from BJP but even more extreme. We cannot have a status quo any longer. Modi has always disrupted the systems he has been in. Now, he needs to disrupt his own being.
Snake with a Venom: Ramdhari Singh Dinkar wrote - "क्षमा शोभती उस भुजंग को, जिसके पास गरल हो| उसका क्या जो विशहीन, विनीत, सरल हो|" - pardon of a weak man has no importance. If you can’t punish someone, then probably implying that you forgive them is pointless. When it comes to punishing the criminals do not let things go their merry way. Take the issue by the scruff of the neck and make things happen. For, if things were on the other foot, that is precisely what your opponents will do. Martyrdom is no claim of bravery. Specifically when you have the power.
Draw your Line: Abuse cannot be a human right. It is not Modi who is abused alone. But increasingly Hindus are abused using Modi, RSS and BJP as proxies. Leicester showed that very clearly. Even Krishna drew his line. Every intelligent leader does that. Maryada is not in waiting for your rout.
Lastly, growth and development is not an easy thing when faced with forces gunning for your blood at all times. Some part of your effort should also be spent in creating a force to fight those battles. Without that there is nothing to bring development to.
India can rise if India remains.