How Tariffs, AI, and Robots Will Reshape Industry and Humanity
Tariffs are breaking old trade ties. AI and robots are rewriting the rules. The U.S.–China split is just the beginning of a new world map drawn in algorithms, not alliances.
Tech startups and social media giants are strongly tied to Intelligence agencies that use them to dominate the world. Espionage wars are being fought in boardrooms. A deep look.


When Dronacharya was confronted by Eklavya with his knowledge that he gained while eavesdropping on the training that the weapons master was giving to Arjun, his dilemma would have been significant.
What was being shared were Siddhis (special, almost superhuman, powers). These brought special powers. Powers that could defeat armies.
It was akin to stealing technical secrets that could only be passed on by a Guru to his/her Disciple in a certain process and set up. It had to be done with a certain integrity.
Eklavya had disrupted the process by creating an espionage technique. Even if it was done innocently.
The ramifications of Siddhis falling in the wrong hands could be immense. The disciples were not just trained in handling the Siddhis but also prepared spiritually to use them correctly at the right time. Without any prejudice. There were very deep and strict rules of how, where, on whom and when could the Siddhis be used. To ensure the person who was getting them would do so meant they had to be prepared for that. While Eklavya may have got the Siddhis, he may not have necessarily been prepared for the spiritual integrity.
One without the other can lead to disasters.
The world of technology innovations and deeply intrusive applications that can start or avert wars is like the world of Siddhis. That is why intelligence agencies and the governments are getting involved. And, while there are Arjuns working to handle the cutting-edge and deep technologies, Eklavyas will be lurking around as well.
The world is changing. Are we all ready?
Silicon Valley is the largest ecosystem for tech startups and innovations on the planet. Great ideas germinate there and blossom into world-beating giants.
And, that creates a power that is hard to pass by. Specifically for the intelligence operations of different countries.
Russia also employs older, tried-and-true methods locally. Intel officials have suspected that Russian spies were enlisting local high-end Russian and Eastern European prostitutes, in a classic Russian “honeypot” maneuver, to gather information from (and on) Bay Area tech and venture-capital executives. Sex workers targeting executives at high-end bars and nightclubs such as the Rosewood Sand Hill, an ultra-luxury hotel located near many of Silicon Valley’s top financial firms—infamous for its raucous, hook-up oriented Thursday nights—the Redwood Room, a tony bar located in the Clift Hotel in downtown San Francisco, and other spots have been identified as potentially reporting back to Russian intel officers, said another former official. (Source: “How Silicon Valley Became a Den of Spies"/Politico)
Prostitutes, honey-pots, Silicon-valley tech entrepreneurs - it was all there.
This is the clandestine part.
In 2016, Harold T. Martin III was arrested on the suspicion of stealing classified information from the National Security Agency (NSA). Harold was a Booz Allen employee. Not many know that Booz Allen has a large revenue portfolio linked to classified American intelligence work.
Booz Allen, a consulting firm that earns billions of dollars by working for American intelligence agencies, has been called the world’s most profitable spy organization. (Source: "At Booz Allen, a Vast U.S. Spy Operation, Run for Private Profit"/New York Times)
Booz Allen is the most profitable spy organization! Who could have thunk?
High-stakes corporate organizations can be and have been fronts for the American and British Intelligence agencies.
Carl Bernstein, the legendary journalist who broke the Watergate scandal teaming up with Bob Woodward, said in his blog (now archived).
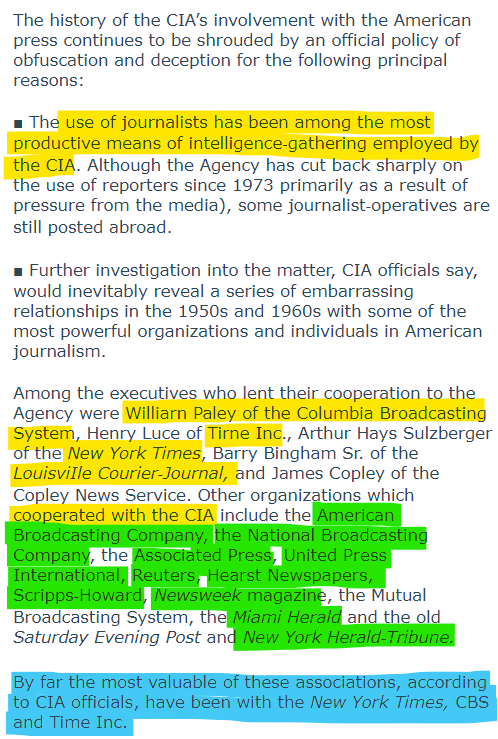
The Pulitzer prize-winning legendary journalist basically says that the entire media is on the payroll of the CIA!
A similar sentiment was echoed by a story in New York Times in 1977.
A December 26, 1977, investigative report in the New York Times described the scope of the CIA’s global campaign to influence opinion through media manipulation. “In its persistent efforts to shape world opinion, the C.I.A. has been able to call upon” an extensive network “of newspapers, news services, magazines, publishing houses, broadcasting stations and other entities over which it has at various limes had some control. A decade ago, when the agency’s communications empire was at its peak, [it] embraced more than 500 news and public information organizations and individuals. According to one CIA official, they ranged in importance ‘from Radio Free Europe to a third‐string guy in Quito who could get something in the local paper.’” The CIA funded those foreign “journalistic assets” generously. (Source: "How the National Security State Manipulates the News Media"/CATO Institute)
After the Vietnam war, CIA officer Frank Snepp shared the modus operandi of how the CIA worked with the journalists to disseminate disinformation. He even shared the names of the journalists, some very popular, whom he had used sometimes without their knowledge.
What does this mean?
The shifts that one sees in terms of media focus and narratives are usually funded, backed, and orchestrated by powerful intelligence agencies as part of an intelligence operation and executed with close cooperation of the media sepoys in the target country and in the US.
How's that for "Freedom of Press"?
Gilman Louie was hired by the CIA to start the work on its Venture Capital arm the In-Q-Tel, where ‘Q' stands for the 'Q' factor from Bond movies. In Bond movies, ‘Q’ is the head of Q Branch, the fictional research and development division of the British Secret Service. This organization was started by George Tenet, the C.I.A. director. He wanted to create a way to invest $30 million a year in internet startups in Silicon Valley. CIA could use it to develop cutting-edge tech that could be used for getting intelligence and could be used for national security.
The directions to him were:
to provide venture capital for data-mining technologies that would allow the C.I.A. to monitor and profile potential terrorists as closely and carefully as Amazon monitors and profiles potential customers. (Source:“Silicon Valley's Spy Game”/New York Times)
The dot-com crash happened in early 2000 and then came 9-11. The tech companies wanted all the money they could find. And, that is when In-Q-Tel came in handy.
The finances for intelligence agencies got a boost when Bush asked for $38 billion in budget and then increases over that.
Mitchell E. Daniels Jr., director of the White House's Office of Management and Budget, said the fiscal 2004 budget that Bush will unveil early next month will include "substantial" increases in homeland defense spending beyond the $38 billion proposed for this year.(Source: “Homeland Security Dept. Faces a Funding Gap for Years”/Washington Post)
Nobody was complaining.
The flavor of the day that the intelligence agencies were after was surveillance technologies.
In Las Vegas, several companies predicted that profiling techniques that are now used to detect credit-card fraud could soon be used to detect potential terrorists. A few weeks later, this prediction turned out to be a reality, when The Washington Post reported that the federal aviation authorities and two technology companies called Accenture and HNC Software are planning to test at airports a profiling system designed to analyze each passenger's living arrangements, travel and real-estate history, along with a great deal of demographic, financial and other personal information. Using data-mining and predictive software, the government then plans to assign each passenger a ''threat index'' based on his or her resemblance to a terrorist profile. Passengers with high threat indexes will be flagged as medium or high risks and will be taken aside for special searches and questioning. (Source: New York Times)
What was In-Q-Tel really investing in? (Source for the companies below: Security Affairs)
The new money from the intelligence sources for the start-ups came to be called "Spooky Finance".
These firms — like New North Ventures, Harpoon, Scout Ventures, and Razor's Edge — are often themselves staffed by former U.S. intelligence and military officials, and sometimes work together to cofund national-security-related startups in areas such as artificial intelligence, cybersecurity, and next-generation communications. The new world of "spooky finance" reveals an increasingly tight relationship between venture capital firms and U.S. spy and military agencies, which have long sought to tap into Silicon Valley’s technology base. (Source: "In Silicon Valley, a new breed of investors is seeking closer ties to America’s military and spy agencies" / Yahoo News)
The interest in AI, data mining and analytics by the CIA coincided with the rise of social media companies. Facebook is one of them.
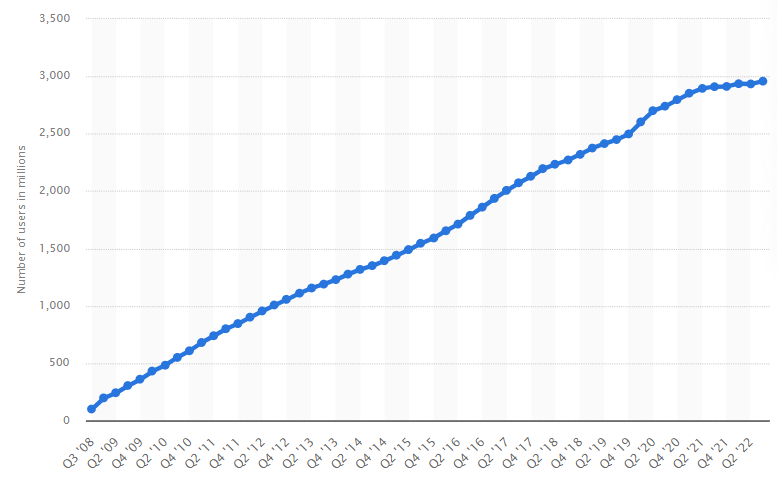
In January 2008, Tom Hodgkinson (editor of the magazine named Idler) wrote in The Age about why the rise of Facebook should be a concern as opposed to be something of an excitement.
At that time Facebook had 59 million active users. Today they are 2.96 billion!
Hodgkinson shared that although Facebook was conceived by "media cover star" Mark Zuckerberg, in reality, it was the Silicon Valley venture capitalist and futurist philosopher Peter Thiel who was the real force behind it.
At that time, there were only three members on its board:
Who is Peter Thiel: Tom shares how Thiel is an eccentric thinker with a strong conservative and even racist outlook on life and the world. For example, Thiel "co-wrote a book called The Diversity Myth, which is a detailed attack on liberalism and the multiculturalist ideology that dominated Stanford. He claimed that the "multiculture" led to a lessening of individual freedoms." (Source: The Age)
Thiel's mentor at Stanford University was Rene Girard who had proposed a theory of human behavior called mimetic desire. It says that "people are essentially sheep-like and will copy one another without much reflection"
Who is Jim Breyer: Now Breyer is the most interesting character in this assembly. Why? Because of the associations, he brings to the table.
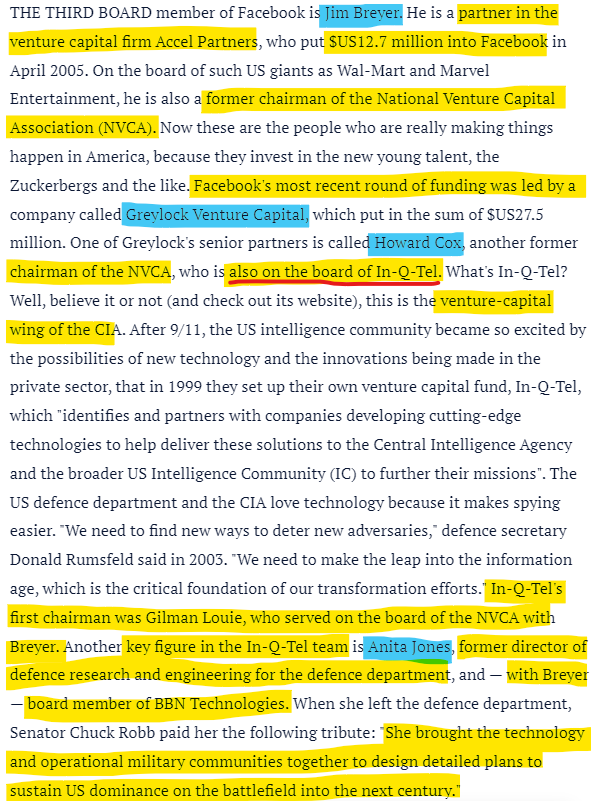
Hodgkinson puts it really well about Facebook back then in 2008.
Now even if you don't buy the idea that Facebook is some kind of extension of the American imperialist program crossed with a massive information-gathering tool, there is no way of denying that as a business, it is pure mega-genius.
So there is a strong connection between the CIA (and other intelligence companies) and Venture Capital outfits other than the In-Q-Tel. Firms like Accel Partners.
In-Q-Tel is becoming an essential clog in a multi-level structure that delegates power to law enforcement and corporate security thru an expanding network of technicians, former intelligence officers, and corporate venture capitalist. Participation in this network via IQT varies depending on the necessities of intelligence gathering.One important figure is Keith Crandell who sits on the board of directors of four different IQT funded companies.As a cofounder of venture capital firm Arch Venture, he’s in position to delegate responsibility, nurture ideals, recruit personnel, and other essential factors in directing the trajectory of future technological innovations.Arch Ventures has provided seed capital for, among other things, the development of laser enhanced electro-optical systems manufacturer Alfalight.Its’ technology is a key component in UAV surveillance.Nano particles used in display technology and energy storage is being advanced by Crandell’s Nanosys, while simultaneously, more molecular research at Quanterix and Boreal Genomics will assist law enforcement in an unique “on-targeting platform” destined for eventual combat operations. Accel Partners plays a similar role as a co-funder with IQT on numerous projects. (Source)
So all these tie-ups and jumping through the hoops for what? What was the CIA and the government planning to do?
That is where John Poindexter comes in.
But before we go there. Please watch this clip from the CBS series "Person of Interest."
Poindexter is a retired United States naval officer and Department of Defense official who was the Deputy National Security Advisor and National Security Advisor during the Reagan administration. He was the Director of the DARPA Information Awareness Office (IAO).
It was Poindexter and SAIC executive Brian Hicks who had approached the US Department of Defense with the idea for an information awareness program.
This is what "Total Information Awareness" set out to do.

In 2003, the US government said that it had "dismantled" the "Total Information Awareness" program.
The Senate today passed legislation that would dismantle the cyber-surveillance program previously called ""Total Information Awareness."" The American Civil Liberties Union hailed the victory and said President Bush should acquiesce to overwhelmingly public concern about privacy rights and allow the program to die. (Source: "CONGRESS DISMANTLES TOTAL INFORMATION AWARENESS SPY PROGRAM" /ACLU)
Officially at least it was "dismantled". Pretended to be so.
In reality, it continued.
In 2012, Wired magazine reported that the program had continued and the National Security Agency (NSA) was building a $2 billion facility in Utah called the "Utah Data Center".
Now, go back to that clip from "Person of Interest" and see what it said. In fact, if you have the time, do watch this entire series. It is an eye-opening experience!
In 2012, the Obama administration announced a “Big Data Research and Development Initiative.” It came with a tag of more than $200 million. (Source: "Big Data is a Big Deal"/Obama White House)
Its goals seemed pretty innocuous.
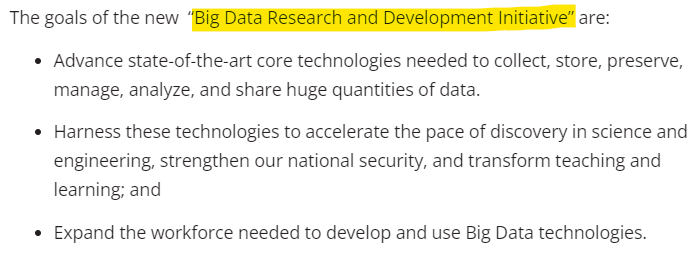
But the Geekwire story shared another initiative that kind of tied everything together.
Meanwhile, the Department of Defense is investing $250 million annually on new ways to “make truly autonomous systems that can maneuver and make decisions on their own.” Other technologies will help military experts extract information from texts in any language, mining the information to make soldiers more prepared on the battlefield. (Source: GeekWire)
The DoD was building "The Machine."
Whatever the government is doing on its own, it is also working with other companies to accentuate or supplement those capabilities. For example, the software called Riot!
Riot is a piece of software that has been developed with help from the US government. It collates social media "check-ins" to dot your movements over Google Maps, and collates your social networking activity to see both who you're friends with, and what you all like to spend your time doing. Add all that shit together and you basically have an algorithm for predicting your behaviour. It's basically like that episode of Black Mirror where a dead man's personality can be replicated from the traces of himself he left behind on social media, but y'know, less Charlie Brooker and more Joe McCarthy. (Source: "Intelligence Agencies Are Using Your Social Media to Spy On You" / Vice)
Per Frank Ahearn – an ex-private detective - Riot was just the starting point. It could be linked to every database and information tool to create a comprehensive surveillance structure around the country. In fact, he relates it to the Total Information Awareness program.
“I take it you’re not familiar with the software TIA (Total Information Awareness) that the United States was working on several years ago?" Ahearn asks me over the phone. Surprisingly, I say, I'm not. "Well," he continues, "it basically takes information from every company out there that keeps databases on their customers. It was supposed to create this huge network of profiles on every single American." TIA was officially canned in 2003 because everyone thought that being spied on really sucked, but many people believe that TIA was just renamed and that the project still unofficially exists. In fact, Riot’s social media analytics could be the final piece of the complete database of American citizens that the Bush administration dreamt of in-between invading countries and rounds of golf. (Source: "Intelligence Agencies Are Using Your Social Media to Spy On You" / Vice)
Riot could be the "final piece" in creating the full database of American citizens.
Yes, it could be.
But what is true of American citizens, could also be true of citizens in other countries as well.
That is precisely why the Chinese government recreated its own social media alternatives and closed down on the American ones.
They just did not want to be part of the whole data pile where every movement, emotion, action, and persona could be monitored, analyzed, and manipulated.
Others had that aspiration too, but they realized it very late. Listen to Varoufakis on this point.
Ioannis "Yanis" Varoufakis is a Greek economist and ex-Minister of Finance.
With technology and cutting-edge data analytical tools being so central to national security and intelligence work, isn't it natural to assume that a place like Silicon Valley would be the place to run your espionage work from if you were Russia, Iran, or China?
After all, getting access to cutting-edge surveillance tech will differentiate the losers from the winners in the coming days.
And, so it was.
As one former senior intelligence official put it: “San Francisco is a trailblazer—you see the changes there in foreign counterintelligence first. Trends emerge there.” If we want to understand a world where Russia and China are ramping up their spy games against the United States, then we need to pay attention to what’s happening in San Francisco. (Source: How Silicon Valley Became a Den of Spies / Politico)
NPR's Hari Sreenivasan had a discussion on this article with the writer Zach Dorfman of POLITICO. The espionage by the Chinese is quite ubiquitous in Silicon Valley.
The future of the world is in tech innovations and discoveries.
And if the surveillance of the populations on the planet is ubiquitous, then it is safe to imagine that the espionage wars will involve isolating the impacts of others' spy efforts and enhancing one's own.
That is where China has been ahead of most non-West countries.
The Indian intelligence agency R&AW uses small companies as go-betweens to access the technologies needed.
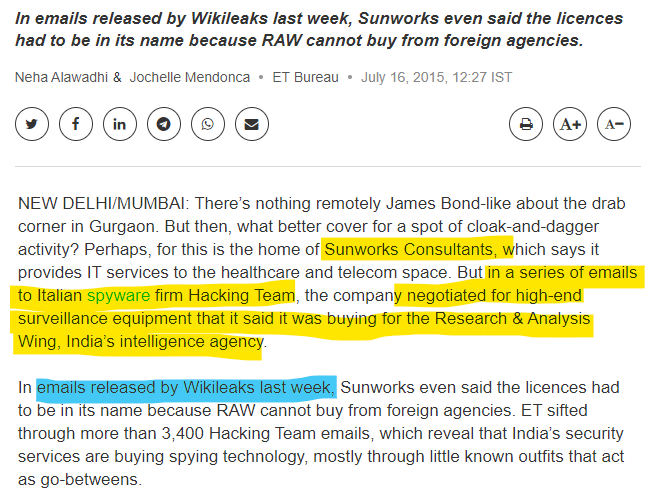
In the new world, where technology has taken over our lives and can provide solid evidence of subversive crimes, Indian intelligence agencies have also moved to the technical side.
In fact, in places like Jammu and Kashmir that are affected by terrorism, 70% to 80% of intelligence inputs are generated through technical intelligence, or TECHINT, which includes telephone records, emails, satellite images, social media posts and other technology-related information. Similarly, over 90% of intelligence gathered and shared everyday by agencies for the rest of India is collected electronically. It is only in the areas affected by Left Wing Extremism (LWE) that Indian agencies mostly depend on human intelligence, or HUMINT, the data suggests. (Source: "India's agencies increasingly depend on tech intel"/Hindustan Times)
In the wild jungle of cybersecurity companies, there are contractors and even specialized companies that offer "vulnerabilities-for-hire" kind of services for those interested.
And, Indian agencies or their proxies use that in the battle with the opponents like China and Pakistan.

Unfortunately, India does what it does using 3rd party resources and tools. While the Five Eyes countries have their own "Machine" along with the means to get the data to feed it with (social media apps that have had the backing of the intelligence agencies)
And, that is where the rub is.
Over the last few years the start-ups in India have increased from 471 in 2016 to 72,993 in 2022. That's a 15,400% growth in the last 6 years! (Source: Times of India)
The start-ups in India specializing in deep-tech like AI, IoT, blockchain, big data and analytics have grown at a compounded annual growth rate (CAGR) of 53% in the last 10 years. (Source: "India's deep-tech startups grew at a CAGR of 53% over 10 years: NASSCOM"/Moneycontrol)
The work for creating the next level of world-beating serious tech companies with government money and oversight in India has just started.
It will bear fruits in the coming years.
But what India really needs to manage its security is to create its own "Machine" and the means to get the data.
That's what the Politico article said.
But what it failed to appreciate was that the battles are happening in tech companies' boardrooms. Unbeknowst to the founders, the workers and the tech nerds.
Who comes out on the top with the most intrusive yet innocuous looking tools will dominate the world and the people of the world.
From now on I will share documentation and links that I saved as part of my research for an article. Many of these links I may have shared in my article and many I would have used in understanding the topics at hand. Beyond this newsletter, I tend to collate all my research even in future into these sub-pages. So bookmark them for future reference. Please feel free to dive in and use it for your own analysis.

It is very rare that the top experts in scientific disciplines come and share the stage with a spiritual master who has viewed things from the "other side". Do the stories match? Do the experiences match?
Does spiritual side go beyond or align with the cutting-edge science of today.
One area of immense interest is "what is Consciousness". The more I have heard of how the scientists have viewed it versus how the spiritual paths point to shows that the science has not fully reached the clarity that spiritual masters have discussed.
This conversations is between Sadhguru and Emery N. Brown, MD, PhD, Warren M. Zapol Professor of Anesthesia at Harvard Medical School and at Massachusetts General Hospital, Edward Hood Taplin Professor of Medical Engineering and Professor of Computational Neuroscience at MIT; and Nicholas D. Schiff, MD, PhD, The Jerold B. Katz Professor of Neurology and Neurosciences, Weill Cornell Medical College, New York.
With that kind of line up from the scientific community, it is interesting how Sadhguru handles their questions.
The conversation remind me of the discussions between Jiddu Krishnamurti and David Bohm, the Nobel Laureate in Physics.
If you like our content and value the work that we are doing, please do consider contributing to our expenses. CHOOSE THE USD EQUIVALENT AMOUNT you are comfortable with.
If you like this post - please share it with someone who will appreciate the information shared in this edition.
Today’s ONLINE PAPER: Check out today’s “The Drishtikone Daily” edition. - THE DRISHTIKONE DAILY